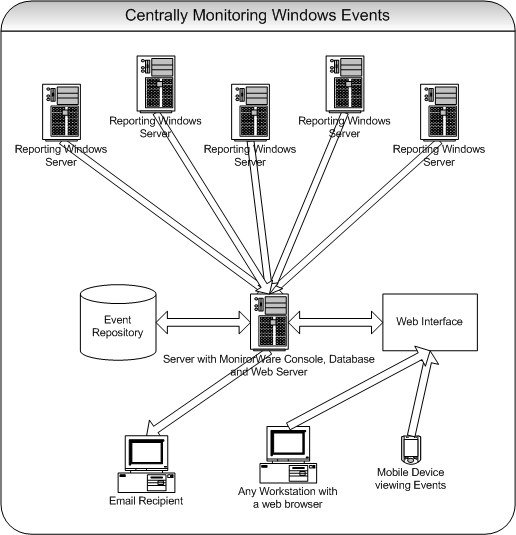
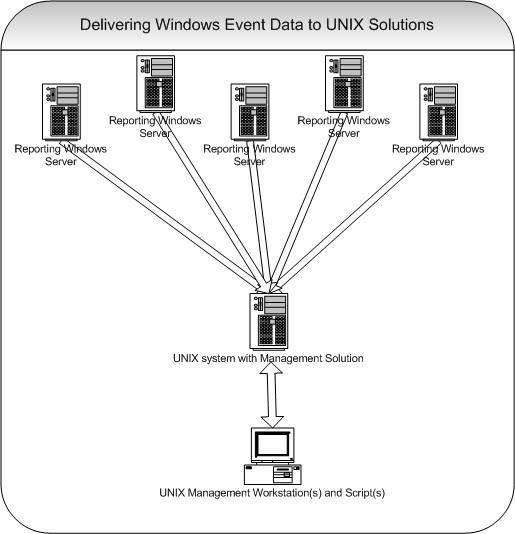
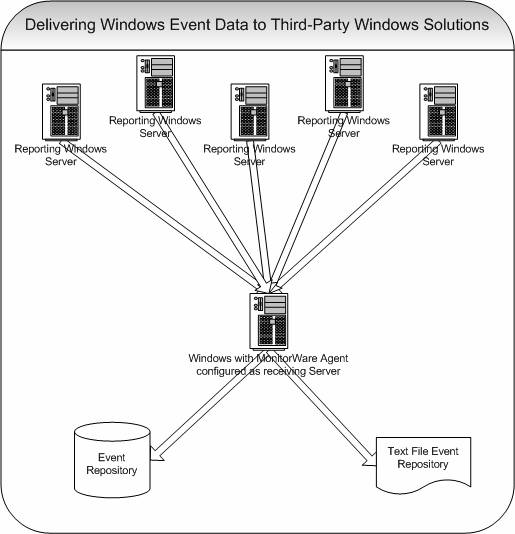
Common uses
Article created 2003-05-14 by Rainer
Gerhards.
Relaying Events
In all but the easiest scenarios event data needs to be relayed between
different machines. Please note that relaying is also often referred to
as “forwarding” – both terms have the same meaning in the context
of this documentation.
A typical relay scenario might look like follows:
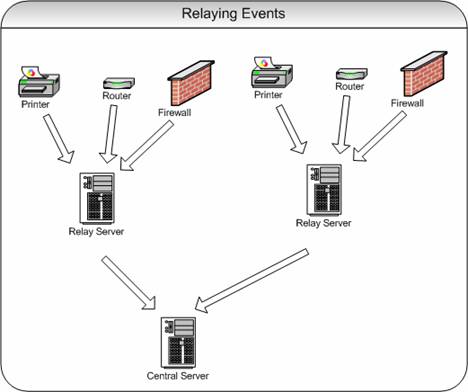
Here, devices send event data to servers configured for relaying. These
servers in turn forward the data to its final destination, the central
server.
Please note that the so-called “Relay Server” need not be limited to the
relay function. It can also perform any other MonitorWare agent function
like data gathering or real time alerting. Also, the devices of course
can include Windows systems monitored by a MonitorWare Agent configured as data gathering- The idea behind the picture is to provide a quick sample – it is in no means complete.
Whenever it comes to relaying messages, an important decision must be made: the protocol used for relaying must be selected. Basically, either syslog or the SETP protocol can be used. This is an important choice, because the two protocols offer very different benefits:
syslog
- supported by virtually all network devices (like routers, firewalls and the like)
- standardized (but not necessarily all devices follow the standard)
- THE universal network event notification protocol
- UDP based, as such event data might be lost in transit
- limited to 1024 characters per event, which is definitely too short for Windows
event log entries (larger messages can be processed by MonitorWare, but
this can result in more likely packet loss) - event source system typically can not be tracked correctly when using inside a cascaded system
- event information for non-original syslog events is lost as they can not be transmitted in native format
SETP
- Adiscon’s proprietary protocol for event notification
- so far, supported by MonitorWare Agent exclusively
- TCP based, reliable delivery possible
- can be used with Windows IPsec
- optimized for event data transmittal
- events are transmitted in native format and thus can be fully reconstructed at
the receiving side - no event size limit
- XML based
Given the advantages, Adiscon recommends using SETP whenever possible. This is then the case when an MonitorWare Agent sends events to another MonitorWare Agent. When events from other devices, e.g. routers, are to be received, syslog protocol must be used for these incoming events. If event data is to be sent to a non-MonitorWare Agent system (e.g. a management system on a Linux or UNIX system), syslog must also be used as these other systems do not “speak” SETP.
MonitorWare Agent can process both of these protocols concurrently. So it is no problem to use SETP in a mixed environment. Again, we highly recommend using SETP whenever possible.