Common uses
Article created 2003-05-14 by Rainer Gerhards.
Updated 2004-06-21 by Tamsila-Q-Siddique.
Analysis
If you are interested in receiving a consolidated view of your overall system
state and activity, you are probably interested in the analysis features of the MonitorWare system.
Please note that this chapter is currently being expanded. As such, the examples and uses given herein do only reflect some of the things that can be done with MonitorWare.
The MonitorWare Agent itself provides the necessary data-gathering facilities to supply event data for analysis. The MonitorWare Agent
itself does not include any analysis feature. As such, it is always teamed up with either other members of the Adiscon MonitorWare line of products or
third party solutions. MonitorWare Agent is also often used to integrate Windows-based event data like Event Log data or IIS log files into UNIX based management solutions.
Centrally Monitoring Windows Event Log Data
In this scenario, you are primarily interested in consolidating Windows Event Log data into a single system. Also, a scheduled overall system activity report should be automatically generated and provided for your review.
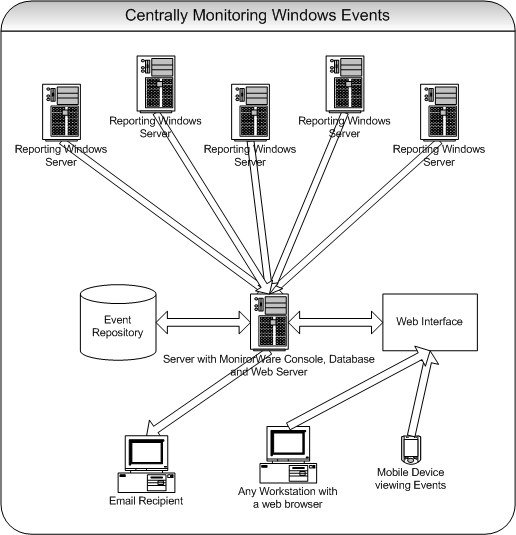
This scenario is so common that we have created a dedicated step-by-step
guide covering all steps necessary. Please find it at “Centralized Event
Reports with MonitorWare Console”.
After following the step-by-step guide, you are encouraged to configure your Windows system to supply as many security related and audit information as needed. This is detailed in
“Configuring Windows for the Event Log Monitor”.
Please note that in default configuration Windows supplies only limited
information and also runs the risk of event loss due to filled-up log
files. Follow the guide to resolve this.
The scenario described can easily be extended to include non-Windows
event data, for example Cisco router logs. These events will also become
part of the MonitorWare Console overview report.
Delivering Windows Event Data to UNIX based Management Solutions
In this scenario, Windows Event data is “just” to be forwarded to a
UNIX based management solution. Most often, the UNIX based solution is
already in operation but lacking Windows event information.
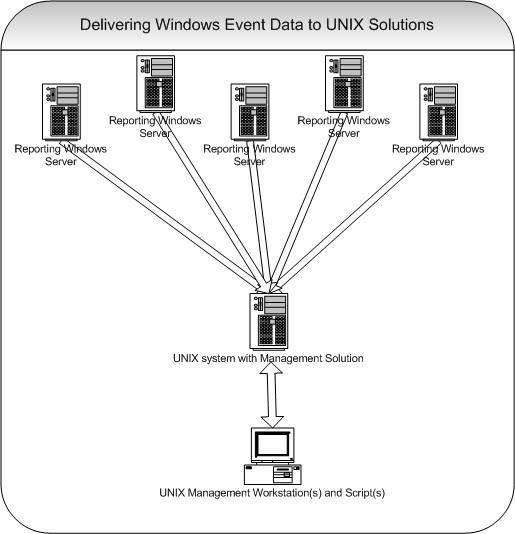
In this scenario, MonitorWare Agent is simply configured to forward
captured events via syslog to a central, UNIX based server. There, the
data is stored and further processed. Most often, customer scripts will
parse the gathered data and perform the actual analysis. The key point
here is that MonitorWare Agent enables these scripts and applications to
process Windows events, which are otherwise unavailable to them.
Please note that “Windows Events” does not only include Windows event log data but also text files like IIS log files.
Delivering Windows Event Data to Windows based Third-Party solutions
In this scenario, Windows event data (including event log data as well as
text files and other supported sources) is delivered to a central
Windows loghost and stored there for further analysis. In contrast to
other scenarios, the analysis part is done by third party software and
– most often in this scenario – customer developed scripts.
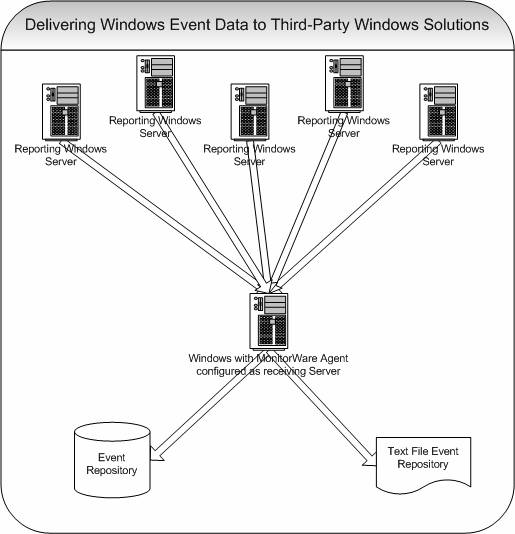
This scenario is not very common, but there are a number of customers with very specific needs that have great success with it. In general, it can
be combined with Adiscon’s analysis tools described in
“Centrally
Monitoring Windows Event Log Data”.
If used without any Adiscon analysis software, events can be written to
whatever source the custom scripts supports, for example text files or
the database.
Delivering Windows Event Data to Third-Party Solutions
There are a number of third party “black boxes” out that can receive and
process Windows events. A popular example is the Counterpane Sentry, a
device that receives Windows event log data via syslog and stores and
processes it. The Sentry is part of Counterpane’s services offering.
For more information, please visit the Counterpane web site at
www.counterpane.com.