Forwarding IIS Logs to a central File
Created 2004-04-02 by Timm Herget and Rainer Gerhards.
I would like to centralize IIS log files to a central log server. The files on that central server should be in the exact same format they are on the IIS machines.
This can be done with MonitorWare Agent 2.0 and above. Let’s look into the theory first: If you would like to forward IIS log files AND have them in the same format at the receiving machine, you need to make some special settings.
First of all, please note that the file monitor, when set to “W3C log files”, is optimized to extract the properties from each log line, not to forward the log literally. If you would like to forward them literally, you need to make sure that the format is set to “Standard”, which will disable all W3C-log specific handling (that would otherwise disturb the result). The syslog tag is not needed here, so it should be totally removed.
We must ensure that the send syslog action does not alter this message content. As such, we must make sure that the “Add Syslog Source when Forwarding” setting is NOT activated.
Unfortunately, that will not eliminate the tag as such from the syslog message, but we can handle this with the property replacer. As of RFC 3164, the syslog tag will be present in the so-generated message. In fact, the message will be “: <ORIGINAL line W3C>” with <ORIGINAL line W3C> literally being the line taken from the W3C log. Effectively, we end up with two extra characters (“: “) at the beginning of the line. Thankfully, we can eliminate these with the property replacer (it is capable of providing substrings of event properties). The message is in the “msg” property. So “%msg:3%” is everything from the third character position up until the end of the line (end position is not specified and so “end of line” is the default). To use the property replacer, we must just the “Write to File” action with “Custom” file format. Then, we can enter an arbriatary string that shall be written to the file. In our case, we use “%msg:3%%$CRLF%”: this instructs the write to file action to first write the original file line and then a Windows newline sequence. The later is needed because it was stripped out by the file monitor.
This looks in the dialogs as follows:
1. Sender : Forward Via Syslog Settings
The “Add Syslog Source when …”-Checkbox MUST be unchecked.
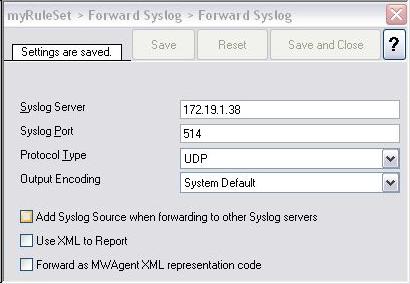
Figure 1: Forward Syslog Action Settings
2. Sender : File Monitor Service Settings
Please note that the “Syslog Tag Value” Field MUST be empty (not even a space in it).
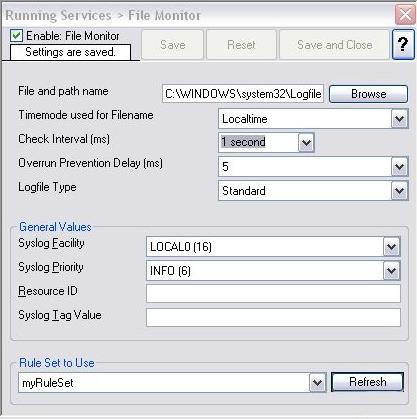
Figure 2: File Monitor Service Settings
3. Recipient: Syslog Listener Settings
Please note that the “Enable RFC 3164 Parsing” MUST be checked
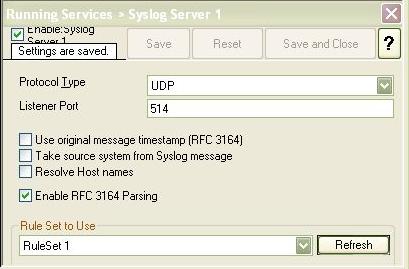
Figure 3: Syslog Listener Service Settings
4. Recipient: Write to File Action Settings
The “File Path Name” Directory must be available, MonitorWare Agent will not create it if its not present.
The “File Format” MUST be set to “Custom”. The following custom line format MUST be used:
%msg:3%%$CRLF%
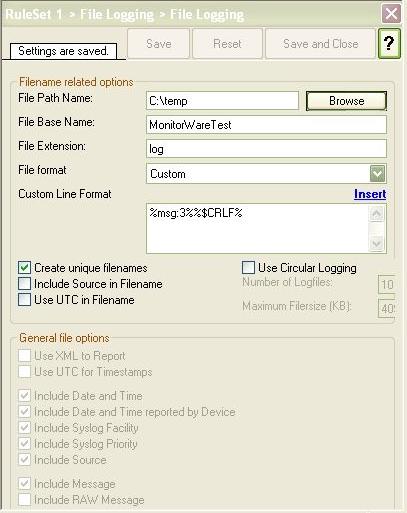
Figure 4: Write to File Action Settings
With the above settings the recipient MonitorWare Agent will successfully generate exact the same logfiles as the original ones are.
Sample Configurations
We have created some registry files for both the sender and the recipient server. If you download them, simply import them into the registry on the machine in question (if you system is a default-install, double-clicking the file is sufficient to do this). Be sure that the MonitorWare Agent client is closed while you do this. Please note that the sample configurations MUST be customized in order to make them work for you.
Sample configuration for MonitorWare Agent 2.0
Please note: samples may not work with versions other than the one specified in the download link!