Step-By-Step Guides
Article created 2003-04-30 by Rainer Gerhards.
Creating a simple Syslog Server
In this scenario, a simple syslog server will be created. No other services are configured. The syslog server will operate as a standard syslog server on the default port of 514/UDP. All incoming data will be written to a single text file.
Step 1 – Defining a Rule Set for File Logging
The rule set specifies what action to carry out. You might be tempted to define the service first, but starting with the rule set makes things easier as it already is present when the service will be defined later and needs to be bound to a rule set.
To define a new rule set, right click “Rules”. A pop up menu will appear. Select “Add Rule Set” from this menu. On screen, it looks as follows:
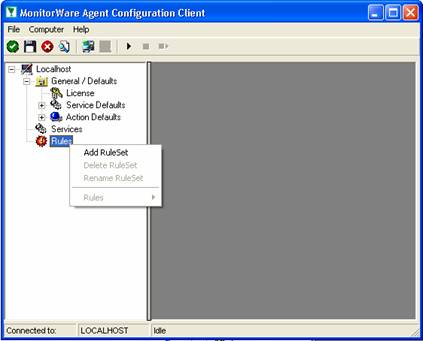
Then,a wizard starts. Change the name of the rule set to whatever name you like. We will use “Write Syslog Log File” in this example. The screen looks as follows:

Click”Next”. A new wizard page appears:

There,select file logging. Do not select any other options for this example. Also, leave the “Create a Rule for each of the following actions” setting selected. Click “Next”.
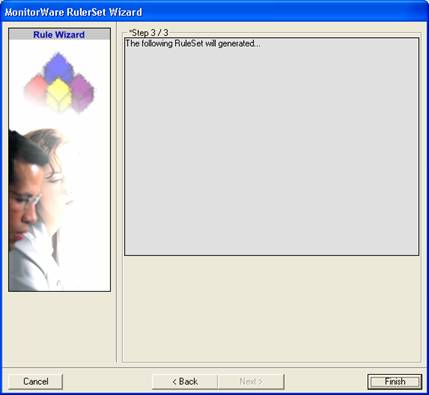
This is just a confirmation page. Click “Finish” to create the rule set.
The wizard closes and the client shows a newly created rule set.

As you can see, the “Write Syslog Log File” rule set is now present. Please expand it in the tree view until you have the following screen contents:

As you can see, we have a “File Logging” action configured. We will review the settings just for your information. Click on “Filter Conditions”:
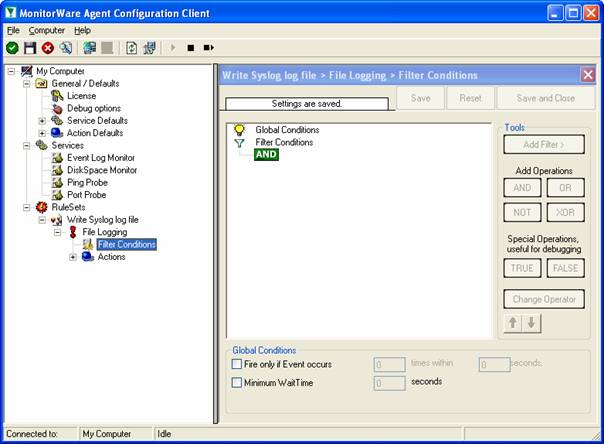
As you can see, none of the filter conditions are enabled. This means that the all information units (incoming messages) will be matched by these filter conditions. As such, the rules for the “File Logging” action will always be carried out.
Please note that this also means that all syslog priorities and facilities will be written to the same file.
Now let us check the “File Logging” action itself. Please select it in the tree view:
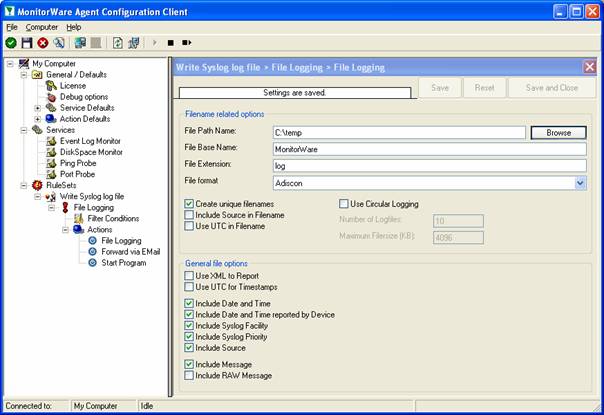
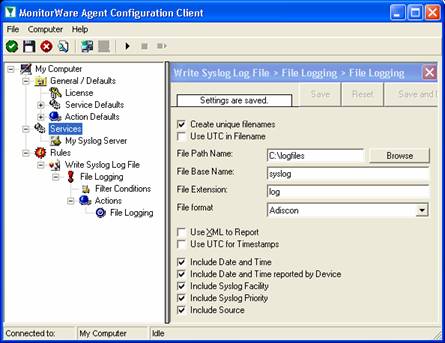
As you can see, it has been created with the default parameters. Each day, a file will be created in the C:\temp directory and its base name will be MonitorWare. It will include all information items in the file.
If you would like to store it into a separate directory or change the file name, here is the place to do it. Important: please make sure the directory you specify exists! If it does not yet exist, please create it before you start the service. If the directory does not exist, the service is not able to store any files.
In our example, we would like to save it to “c:\logfiles” with a base name of “syslog”. Therefore, we change these properties:
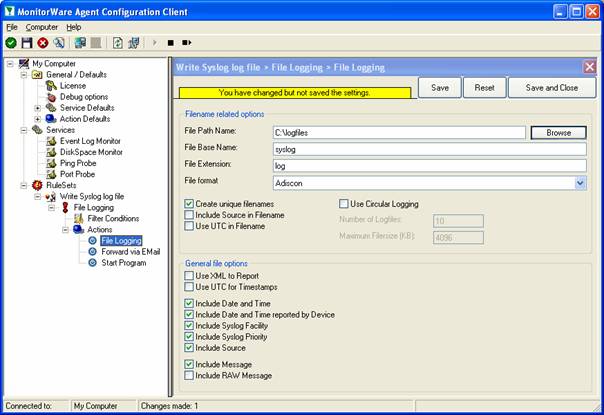
After doing so, you will notice the yellow text on top of the window. It tells you that the configuration changes have not yet been applied. To do so, press “save”.
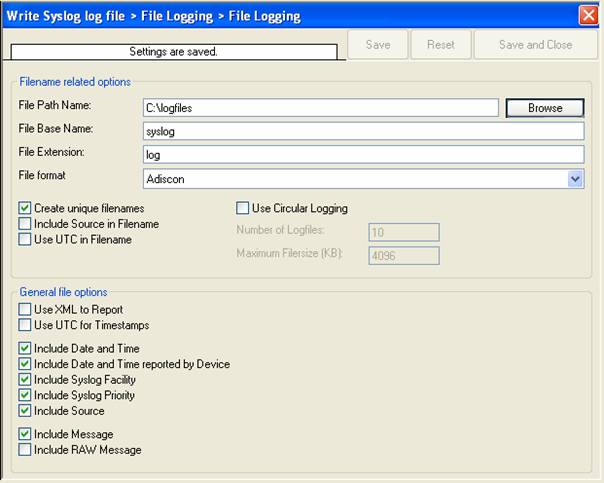
Now you have a workable rule set for logging incoming messages to a text file.
Step 2 – Create a Syslog Server Service
Now we need to define a syslog server service. A syslog server is also sometimes called a “syslog daemon”, “syslogd” or “syslog listener”. It is the process that receives incoming messages.
To define it, right click on “Services”, then select “Add Service” and the “Syslog Server”:
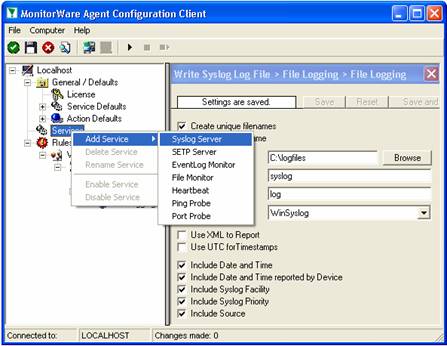
Once you have done so, a new wizard starts:

Again, you can use either the default name or any one you like. We will use “My Syslog Server” in this example. Leave the “Use default settings” selected and press “Next”:
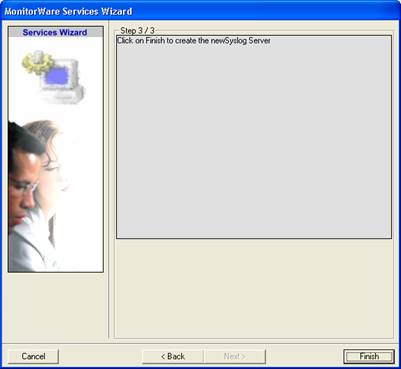
As we have used the default, the wizard will immediately proceed with step 3, the confirmation page. Press “Finish” to create the service. The wizard completes and returns to the configuration client. There, you will see the newly created service beneath the “Services” part of the tree view:
To check its parameters, select it:
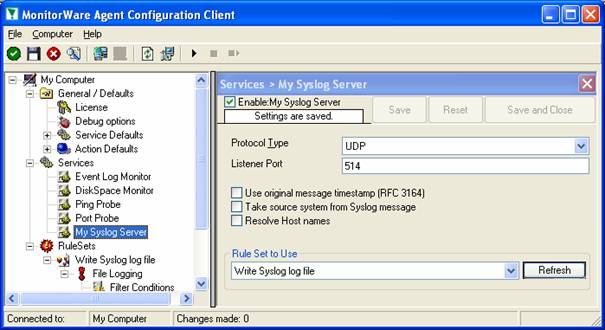
As you can see, the service has been created with the default parameters. As such, it operates as a RFC compliant standard syslog server.
Please note that the “Write Syslog Log File” has been automatically assigned as the rule set to use. This is the case because we already created it and it is the only rule set. By default, the wizard will always assign the first rule set visible in the tree view to new services. If another one is to be used, you need to change it to the correct one here in the service definition.
Also, ote that the wizard uses the default properties from the “Service Defaults”. Obviously, if these are changed, the default properties for new services will differ.
This procedure completes the configuration of the syslog server.
Step 3 – (Re-) Start the MonitorWare Agent Service
MonitorWare Agent cannot dynamically read changed configurations. As such, it needs to be restarted after such changes. In our example, the service was not yet started, so we simply need to start it. If it’s already running, you need to restart it.
Service control can be done with both the respective operating system capabilities (like service manager MMC) or with the configuration client. These are shown in the red surrounded area in the following screen shot:
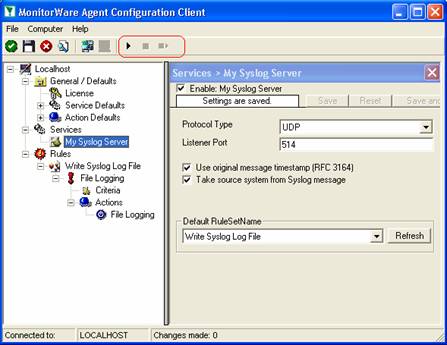
The buttons resemble Windows service manager – start, stop and restart. In this example, stop and restart are grayed out because the service is not running.
After service restart, the new definitions are active and MonitorWare Agent is ready to accept and store incoming messages.
Step 4 – Configure your Syslog-Enabled Devices
Even though MonitorWare Agent is now ready, it can only receive messages if some devices send them. Remember, syslog is a protocol where the server is passively waiting for incoming messages. As long as no device sends message, the syslog server will not log anything.
Since there are a large variety of devices, we unfortunately cannot provide device specific instructions. However, almost all devices need to be configured with their specific configuration tool. Typically, only two settings need to be made: one to activate syslog messages at all and one with the syslog server IP address or name.
For some devices, we have step-by-step guides. Please read “Sample Syslog Device Configurations” for further details.
Remember: the computer running MonitorWare Agent now acts as a syslog server. As such, you need to find out its IP address or name and supply it to the device as the syslog server. Please note that not all devices can operate with computer names. Use the IP address, if in doubt.
400-201 Study Guides ,
70-980 Study Guides ,
640-911 exam ,
SSCP certification ,
70-177 Brain dumps ,
220-901 pdf ,
2V0-621 test ,
70-410 Brain dumps ,
640-916 certification ,
1Z0-051 Study Guides ,
220-801 Exam ,
LX0-104 certification ,
1Y0-201 pdf ,
OG0-093 certification ,
1V0-601 certification ,
LX0-104 test ,
350-060 exam ,
200-101 pdf ,
1z0-808 Study Guides ,
300-209 dumps ,
PMP certification ,
EX300 test ,
JN0-102 certification ,
70-177 pdf ,
640-916 pdf ,
000-104 test ,
CAS-002 dumps ,
300-075 certification ,
350-001 test ,
100-101 test ,
70-533 certification ,
2V0-621D test ,
070-461 test ,
640-692 Study Guides ,
70-413 Study Guides ,
70-411 test ,
1Z0-051 dumps ,
200-310 pdf ,
70-463 Study Guides ,
700-501 certification ,
1Z0-804 exam ,
810-403 dumps ,
70-347 pdf ,
OG0-093 dumps ,
352-001 pdf ,















