MonitorWare Agent 3.1 Released
Build-IDs: Service 3.1.292, Client 3.1.889
New Minor Additions |
|
Log Consolidator and Alerter
Build-IDs: Service 3.1.292, Client 3.1.889
New Minor Additions |
|
Article created 2003-02-24 by Rainer Gerhards.
Last Updated 2011-05-25 by Tom Bergfeld.
Starting with EventReporter 8.3 and MonitorWare Agent 4.3 two different event log monitor services are provided. They are called “Event Log Monitor” (V1) and “Event Log Monitor V2”. In short, the V2 version is recommended for Windows Vista (and above, e.g. Longhorn Server) while the other version is for previous releases of Windows (NT, 2000, 2003, XP). Please find more information about the different EventLogMonitors at Which Event Log Monitor to use.
There is also a guide How To setup EventLogMonitor V2 Service.
1. First, right click on “Services”, then select “Add Service” and then “Event Log Monitor”:
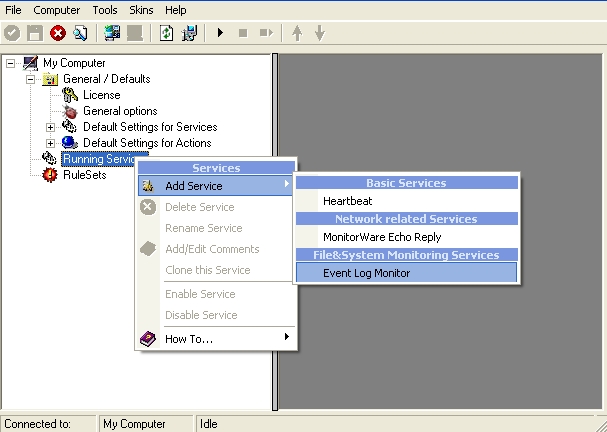
2. Once you have done so, a new wizard starts.
If the following Popup appears, please select “Create Service”:
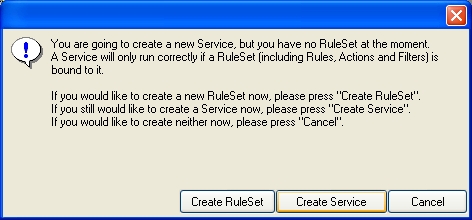
Again, you can use either the default name or any one you like. We will use “My Event Log Monitor” in this sample. Leave the “Use default settings” selected and press “Next”.
3. As we have used the default, the wizard will immediately proceed with step 3, the confirmation page. Press “Finish” to create the service. The wizard completes and returns to the configuration client.
4. Now, you will see the newly created service beneath the “Services” part of the tree view. To check its parameters, select it:
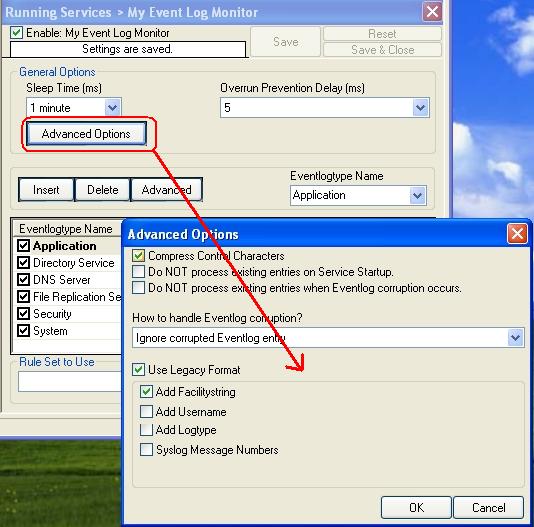
As you can see, the service has been created with the default parameters.
Note 1: The “Default RuleSet” has been automatically assigned as the rule set to use. By default, the wizard will always assign the first rule set visible in the tree view to new services. In our case, this is not correct and will be corrected soon.
Note 2: If you want to generate reports (using Monilog) on the data via this service i.e. EventLogMonitor, then you have to press the “Configure for Monilog” button and make the settings as shown in the screen-shot.
Note 3: If you want to generate reports (using MonitorWare Console) on the data via this service i.e. EventLogMonitor, then you have to uncheck the “Use Legacy Format” option. This is recommended. If you don’t uncheck this option then meaningful reports aren’t generated (i.e. reports are not properly consolidated by MonitorWare Console).
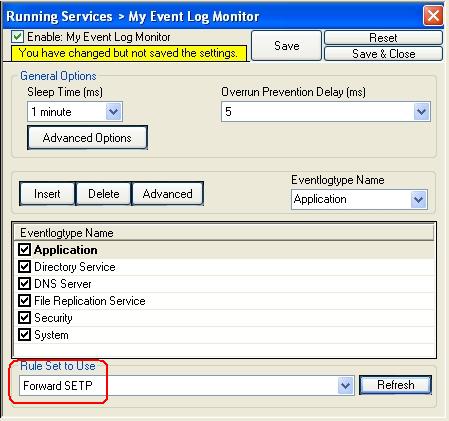
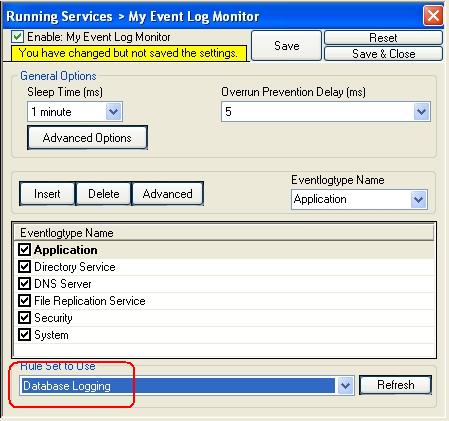
5. Now you must differentiate between clients and central hub server. In clients use the “Forward ” RuleSet we have created in Step 2, select it as rule set to use. In central hub server select the “Database Logging” RuleSet we have created in Step 3. Leave all other settings in their default.
Clients:
Central hub server:
6. Finally, save the change and start MonitorWareAgent. This procedure completes the configuration of the syslog server.
MonitorWare Agent cannot dynamically read changed configurations. As such, it needs to be restarted after such changes. In our sample, the service was not yet started, so we simply need to start it. If it already runs, you need to restart it.
With step 5 the client machines configuration has finished. All the next steps are only concerned with the central hub server.
Article created 2003-04-30 by Rainer Gerhards.
Last Updated 2005-08-16 by Timm Herget.
In this scenario, an event log monitor is used to forward all events written to the NT Event Log to a syslog server. This can either be another instance of MonitorWare or any standard syslog server, for example on a UNIX platform. The data will be forwarded in the EventReporter compatible format, as the processes running on the syslog server require that format (this is just an assumption).
This is a scenario often used together with UNIX based management solutions. The event log monitor is used here to forward events into a central repository, where it will be analyzed using pre-existing procedures.
Please note that if the data is to be forwarded to another instance of a MonitorWare Agent, we highly recommend using the SETP protocol instead of syslog – but this is beyond the scope of this scenario here.
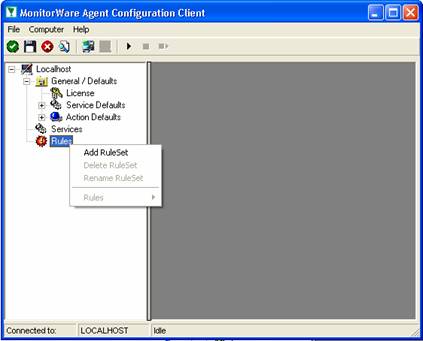
The rule set specifies what action to carry out. You might be tempted to define the service first, but starting with the rule set makes things easier as it already is present when the service will be defined later and needs to be bound to a rule set.
To define a new rule set, right click “Rules”. A pop up menu will appear. Select “Add Rule Set” from this menu. On screen, it looks as follows:
Then, a wizard starts. Change the name of the rule set to whatever name you like. We will use “Forward To Syslog Server” in this example. The screen looks as follows:
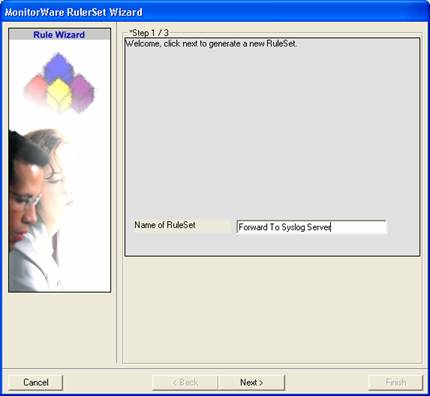
Click “Next”. A new wizard page appears:
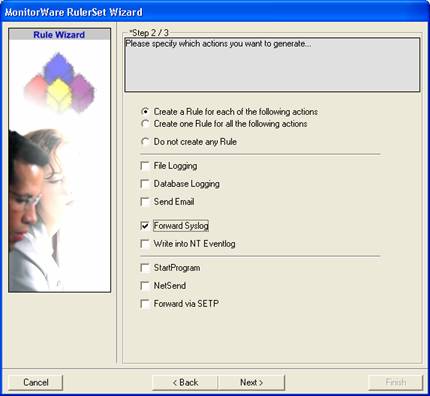
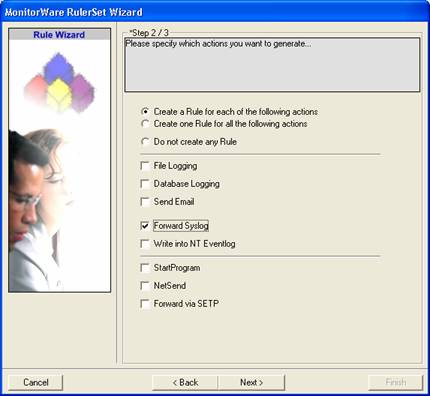
There, select “Forward Syslog”. Do not select any other options for this sample. Also, leave the “Create a Rule for each of the following actions” setting selected. Click “Next”.
This is just a confirmation page. Click “Finish” to create the rule set.
The wizard closes and the client shows a newly created rule set.
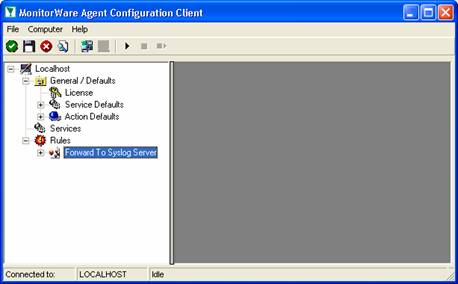
As you can see, the “Forward To Syslog Server” rule set is now present. Please expand it in the tree view until you have the following screen contents:
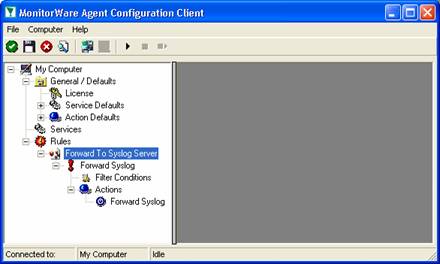
As you can see, we have a “Forward Syslog” action configured. We will review the settings just for your information. Click on “Filter Conditions”:
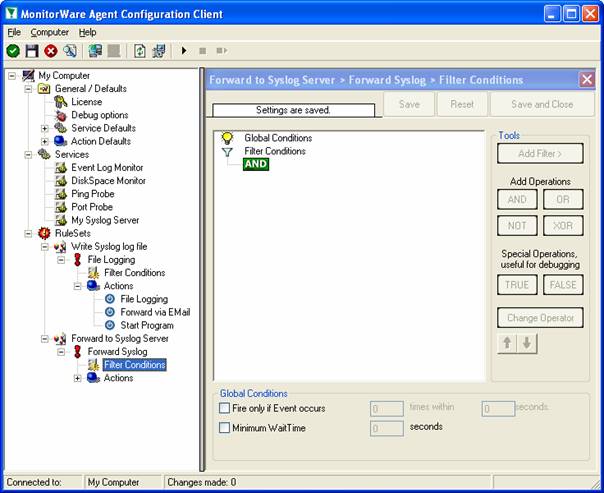
As you can see, no filter conditions are selected. This means that the all information units (the event log information) will be matched by these filter conditions. As such, the rules for the “Forward Syslog” action will always be carried out.
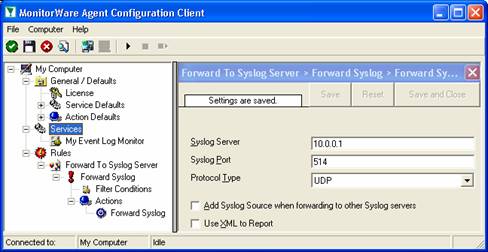
Now let us check the “Forward Syslog” action itself. Please select it in the tree view:
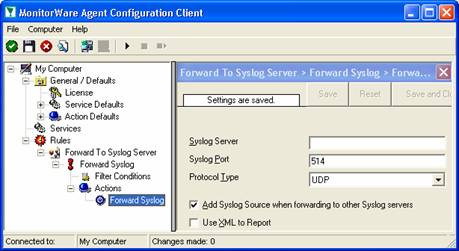
As you can see, some useful defaults are already there. It forwards syslog messages via the standard UDP protocol to the standard port of 514. These values are specified by the syslog standard and most syslog servers will expect them. Only change them if you definitely know that the syslog server is configured to use other values. If in doubt, use the default ones.
However, there are also some things that need to be completed and changed for this scenario.
Obviously, the syslog server to receive the message needs to be specified. You can use either a system name or IP address. In our sample, we will use the IP address, because this is faster and more reliable as it does not depend on DNS name resolution. Our target syslog server is on address 10.0.0.1.
Next, we will uncheck the “Add Syslog Source when forwarding…” options. This option is useful when messages are to be forwarded to the WinSyslog Interactive Syslog Server for instant review. If forwarded to a “real” syslog server, it typically is not useful and might influence the receiving syslog server’s capability to correctly check the message contents.
The “Use XML to Report” option is left unchecked because in this scenario there are pre-existing scripts on the syslog server that expect EventReporter legacy format. The XML option is not compatible with that format.
After the changes, the dialog looks as follows:
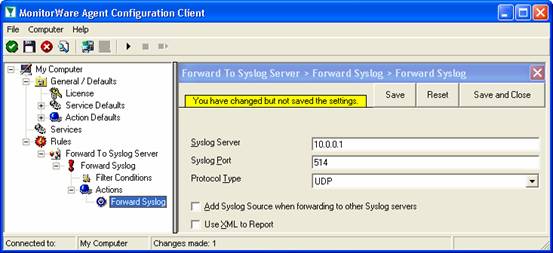
After doing so, you will notice the yellow text on top of the window. It tells you that the configuration changes have not yet been applied. To do so, press “save”.
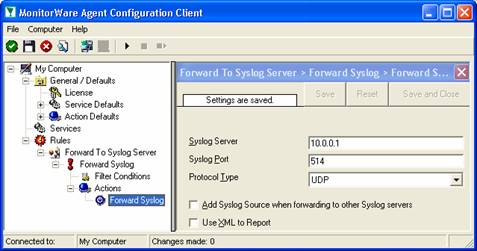
Now you have a workable rule set for forwarding event monitor data to the syslog server.
Now we need to define an “event log monitor” service. It is the process that monitors the Windows event log for new entries and creates information units as soon as a new entry is found. These information units are then passed to the rule set which in turn forwards them to the syslog server configured in step 1.
To define the event log monitor, right click on “Services”, then select “Add Service” and the “Event Log Monitor”:
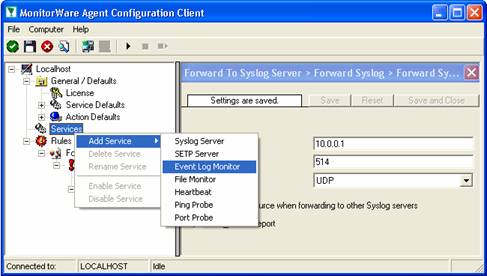
Once you have done so, a new wizard starts:
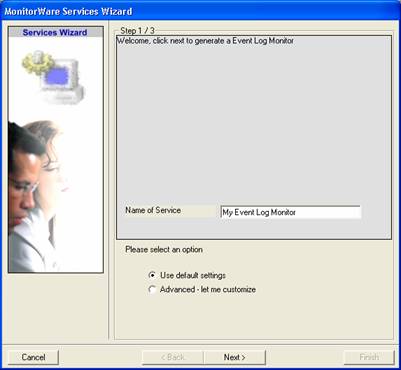
Again, you can use either the default name or any one you like. We will use “My Event Log Monitor” in this sample. Leave the “Use default settings” selected and press “Next”:
As we have used the default, the wizard will immediately proceed with step 3, the confirmation page. Press “Finish” to create the service. The wizard completes and returns to the configuration client. There, you will see the newly created service beneath the “Services” part of the tree view:
To check its parameters, select it:
As you can see, the service has been created with the default parameters. As such, it monitors all event logs that are present on the system. It also has some protection against overruns of the receiving system or intermediary routers. It monitors the event log in a 60 second interval (sleep time of 60.000 milliseconds), which is the recommended value for typical installations.
Please note that the “Forward To Syslog Server” rule set has been automatically assigned as the rule set to use. This is the case because we already created it and it is the only rule set. By default, the wizard will always assign the first rule set visible in the tree view to new services. If that is not the intended rule set, you need to change it to the correct one here in the service definition.
Also, please note that the wizard uses the default properties from the “Service Defaults”. Obviously, if these are changed, the default properties for new services will differ.
There is one change we need to make to the service properties: that is the “Use Legacy Format” option. As specified in the scenario, some pre-existing scripts at the syslog server expect the EventReporter legacy format. As such, we need to check that option:
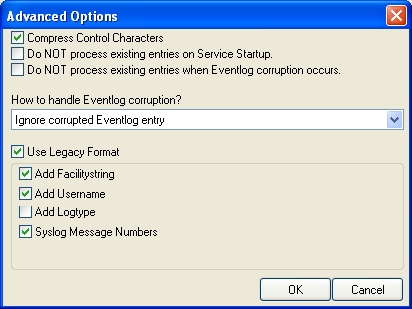
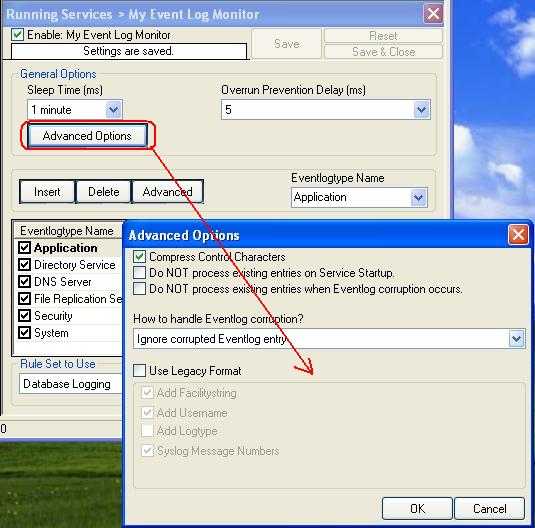
Finally, we review the log specific advanced properties. As a sample, we will go over the application log advanced properties. To do so, click the “Advanced” button:
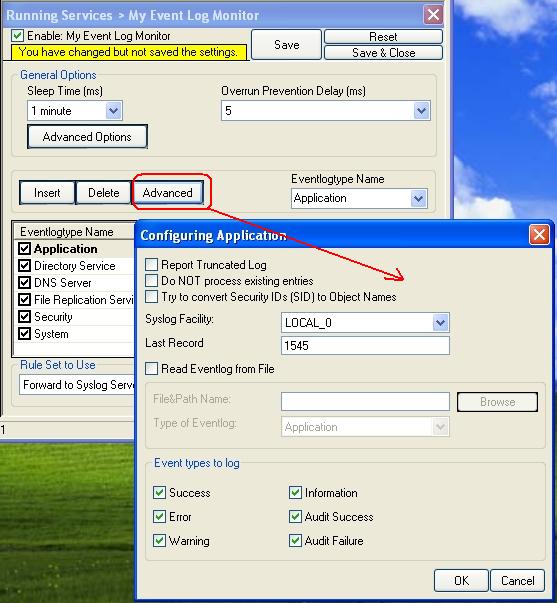
Most importantly, we can select the syslog facility that is to be used for the generated information units here. In our sample, we leave it as local. We also leave the “Report Truncated Log” option checked. This option will generate a warning message if the respective Windows log is truncated, for example by operator request. If that happens during day-to-day operations in you environment, you might want to uncheck it.
Click OK to return to the main property sheet.
This procedure completes the configuration of the event log monitor.
MonitorWare Agent cannot dynamically read changed configurations. As such, it needs to be restarted after such changes. In our sample, the service was not yet started, so we simply need to start it. If it already runs, you need to restart it.
Service control can be done with both the respective operating system capabilities (like service manager MMC) or with the configuration client. These are shown in the red surrounded area in the following screen shot:
The buttons resemble Windows service manager – start, stop and restart. In this sample, stop and restart are grayed out because the service is not running.
After service restarts, the new definitions are active and MonitorWare Agent will forward all events from the Windows event log to the configured syslog server. Please note that on the first run, all already existing events will be forwarded. Therefore, this might take a little while. On all successive service start, only new events will be forwarded.
Article created 2003-04-30 by Rainer Gerhards.
Last Updated 2005-08-16 by Timm Herget.
In this scenario, an event log monitor is used to forward all events written to the NT Event Log to a syslog server. This can either be another instance of MonitorWare or any standard syslog server, for example on a UNIX platform. The data will be forwarded in the EventReporter compatible format, as the processes running on the syslog server require that format (this is just an assumption).
This is a scenario often used together with UNIX based management solutions. The event log monitor is used here to forward events into a central repository, where it will be analyzed using pre-existing procedures.
Please note that if the data is to be forwarded to another instance of a MonitorWare Agent, we highly recommend using the SETP protocol instead of syslog – but this is beyond the scope of this scenario here.
The rule set specifies what action to carry out. You might be tempted to define the service first, but starting with the rule set makes things easier as it already is present when the service will be defined later and needs to be bound to a rule set.
To define a new rule set, right click “Rules”. A pop up menu will appear. Select “Add Rule Set” from this menu. On screen, it looks as follows:

Then, a wizard starts. Change the name of the rule set to whatever name you like. We will use “Forward To Syslog Server” in this example. The screen looks as follows:

Click “Next”. A new wizard page appears:
There, select “Forward Syslog”. Do not select any other options for this sample. Also, leave the “Create a Rule for each of the following actions” setting selected. Click “Next”.

This is just a confirmation page. Click “Finish” to create the rule set.
The wizard closes and the client shows a newly created rule set.

As you can see, the “Forward To Syslog Server” rule set is now present. Please expand it in the tree view until you have the following screen contents:

As you can see, we have a “Forward Syslog” action configured. We will review the settings just for your information. Click on “Filter Conditions”:

As you can see, no filter conditions are selected. This means that the all information units (the event log information) will be matched by these filter conditions. As such, the rules for the “Forward Syslog” action will always be carried out.
Now let us check the “Forward Syslog” action itself. Please select it in the tree view:

As you can see, some useful defaults are already there. It forwards syslog messages via the standard UDP protocol to the standard port of 514. These values are specified by the syslog standard and most syslog servers will expect them. Only change them if you definitely know that the syslog server is configured to use other values. If in doubt, use the default ones.
However, there are also some things that need to be completed and changed for this scenario.
Obviously, the syslog server to receive the message needs to be specified. You can use either a system name or IP address. In our sample, we will use the IP address, because this is faster and more reliable as it does not depend on DNS name resolution. Our target syslog server is on address 10.0.0.1.
Next, we will uncheck the “Add Syslog Source when forwarding…” options. This option is useful when messages are to be forwarded to the WinSyslog Interactive Syslog Server for instant review. If forwarded to a “real” syslog server, it typically is not useful and might influence the receiving syslog server’s capability to correctly check the message contents.
The “Use XML to Report” option is left unchecked because in this scenario there are pre-existing scripts on the syslog server that expect EventReporter legacy format. The XML option is not compatible with that format.
After the changes, the dialog looks as follows:

After doing so, you will notice the yellow text on top of the window. It tells you that the configuration changes have not yet been applied. To do so, press “save”.

Now you have a workable rule set for forwarding event monitor data to the syslog server.
Now we need to define an “event log monitor” service. It is the process that monitors the Windows event log for new entries and creates information units as soon as a new entry is found. These information units are then passed to the rule set which in turn forwards them to the syslog server configured in step 1.
To define the event log monitor, right click on “Services”, then select “Add Service” and the “Event Log Monitor”:

Once you have done so, a new wizard starts:

Again, you can use either the default name or any one you like. We will use “My Event Log Monitor” in this sample. Leave the “Use default settings” selected and press “Next”:

As we have used the default, the wizard will immediately proceed with step 3, the confirmation page. Press “Finish” to create the service. The wizard completes and returns to the configuration client. There, you will see the newly created service beneath the “Services” part of the tree view:

To check its parameters, select it:

As you can see, the service has been created with the default parameters. As such, it monitors all event logs that are present on the system. It also has some protection against overruns of the receiving system or intermediary routers. It monitors the event log in a 60 second interval (sleep time of 60.000 milliseconds), which is the recommended value for typical installations.
Please note that the “Forward To Syslog Server” rule set has been automatically assigned as the rule set to use. This is the case because we already created it and it is the only rule set. By default, the wizard will always assign the first rule set visible in the tree view to new services. If that is not the intended rule set, you need to change it to the correct one here in the service definition.
Also, please note that the wizard uses the default properties from the “Service Defaults”. Obviously, if these are changed, the default properties for new services will differ.
There is one change we need to make to the service properties: that is the “Use Legacy Format” option. As specified in the scenario, some pre-existing scripts at the syslog server expect the EventReporter legacy format. As such, we need to check that option:

Finally, we review the log specific advanced properties. As a sample, we will go over the application log advanced properties. To do so, click the “Advanced” button:

Most importantly, we can select the syslog facility that is to be used for the generated information units here. In our sample, we leave it as local. We also leave the “Report Truncated Log” option checked. This option will generate a warning message if the respective Windows log is truncated, for example by operator request. If that happens during day-to-day operations in you environment, you might want to uncheck it.
Click OK to return to the main property sheet.
This procedure completes the configuration of the event log monitor.
MonitorWare Agent cannot dynamically read changed configurations. As such, it needs to be restarted after such changes. In our sample, the service was not yet started, so we simply need to start it. If it already runs, you need to restart it.
Service control can be done with both the respective operating system capabilities (like service manager MMC) or with the configuration client. These are shown in the red surrounded area in the following screen shot:
The buttons resemble Windows service manager – start, stop and restart. In this sample, stop and restart are grayed out because the service is not running.
After service restarts, the new definitions are active and MonitorWare Agent will forward all events from the Windows event log to the configured syslog server. Please note that on the first run, all already existing events will be forwarded. Therefore, this might take a little while. On all successive service start, only new events will be forwarded.
Created 2005-08-02 by Timm Herget
What are the settings that I would have to make such that the log file is generated in a format that is acceptable to Monilog?
There are a few things that have to be set in order to generate a log file that would be read by Monilog for Reporting purposes
1. Event Log Monitor Setting
The following checkboxes should be checked for Event Log Monitor Service. This must be done by clicking the “Advanced Options” tab. The rest of the “base options” should be leaved at default settings:
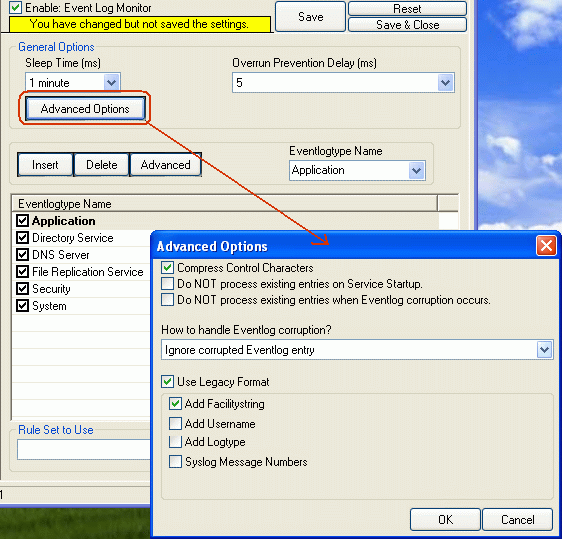
Figure 1: Event Log Monitor Service Settings
2. Forward Via Syslog Settings
In Forward via Syslog Action, you would see a “Message Format” option. From the “Insert” menu entry select “Replace with Monilog Format“. Please Note: It is very important that you uncheck the “Add Syslog Source when forwarding to other Syslog servers” Option. Your settings should be like this:
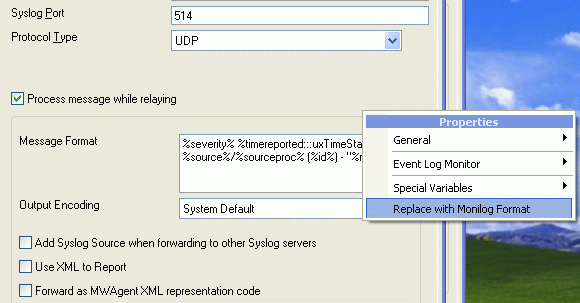
Figure 2: Forward Via Syslog Action Settings
3. Syslog Listener Settings
Please note that the “Enable RFC 3164 Parsing” should be checked
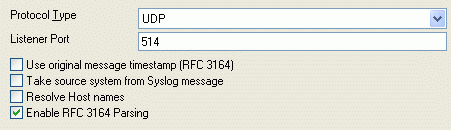
Figure 3: Syslog Listener Service Settings
4. Write to File Action Settings
Please note that you should leave all settings at the default settings for “FileLogging Action”. If you changed anything in your default options, please adapt your settings to those who are shown on the following screenshot:
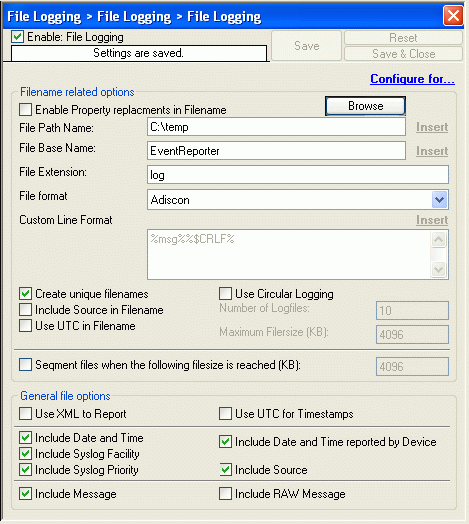
Figure 4: Write to File Action Settings
With the above mentioned settings, Monilog will successfully generate the report on the log file that has been generated.
Article created 2005-04-21 by Hamid Ali Raja
Last Updated 2005-08-02 by Timm Herget
Windows NT/2000/XP/2003 systems monitoring is really important for all small to large sized enviroments. MonitorWare line of products helps to accomplish this important task. This article is to help you establish a small setup to monitor your Windows NT/2000/XP and 2003 systems.
This article is strictly task focused. It does not describe why the systems should be monitor nor does it provide any further background. Please see the respective backgrounders or each of the products documentation on this. This article is a step-by-step description of what you need to do in order to centrally monitor your Windows NT/2000/XP and 2003 systems.
This article has been extracted from the MonitorWare Agent documentation. Please be sure to check the MonitorWare Agent online help if a newer version is available.
In this step-by-step guide, MonitorWare Agent is configured to work together with Adiscon’s MonitorWare Console to automatically generate event summaries for the monitored servers and other devices.
This guide focuses on a typical small to medium business topography with a single geographical location and 5 Windows clients and a central hub server. All systems are well connected via a local Ethernet. Event reports from all machines should be stored in a database. The administrator shall receive daily consolidated event reports.
In this guide, I am focusing on building a solution with Adiscon’s MonitorWare Agent and MonitorWare Console. This combination allows you to centralize all your event logs and report events from them. Free 30 day trial versions are available at the respective product sites (links below), so you can try the system without the need to buy anything.
You need to run the following products:
To deliver MonitorWare Console’s reports, you need a local web server (for example Microsoft’s IIS or Apache) and a mail server capable of talking SMTP (most modern servers support this)
You need administrative privileges on each of the machines. This is required both for installation and configuration. Make sure you log on with a sufficiently privileged user account.
As you read the MonitorWare Agent manual, you most probably downloaded the MonitorWare Agent. If you haven’t, please visit www.mwagent.com/en/download to do so. In addition to the agent, you also need MonitorWare Console. A free, full-featured 30 day trial is available at http://www.mwconsole.com/en/download/.
Run the MonitorWare Agent setup program on all systems that should be monitored. This means you need to run it on all 5 clients and the central hub server. Take a note of the central hub server IP address or host name. You’ll need this value when configuring the agents on the client machine. For our example, we assume this system has an IP address of 192.168.0.1.
For larger installations (with many more servers) there are ways to set it up in a simpler fashion, but in a scenario like ours, it is faster to install it on each machine manually. You can install it with the default settings. When setup has finished, the program automatically is configured to operate as a simple syslog server. However, it does not yet create the log in our database we need. So we will go ahead and change this on each of the machines or by launching it on one machine and remotely connecting to the others. It is your choice. In this sample, I use the MonitorWare Agent on each machine (it is easier to follow).
The steps to configure the agents are as follows (repeat this on each of the 5 client machines). This step needs not to be done on the central hub server!:
1. Start the application.
2. Selected language is English.
3. Then define a new rule set, right click “Rules”. A pop up menu will appear. Select “Add Rule Set” from this menu. On screen, it looks as follows:
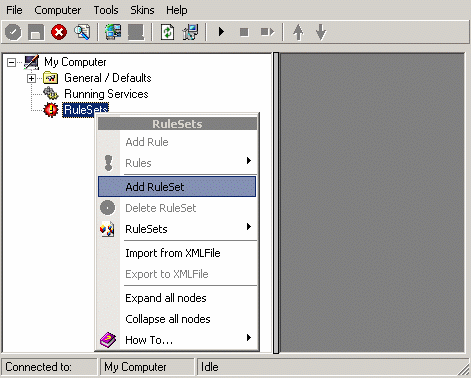
4. Then, a wizard starts. Change the name of the rule to whatever name you like. We will use “Forward SETP” in this example. The screen looks as follow:
Click “Next”. A new wizard page appears.
5. Select only Forward by SETP. Do not select any other options for this sample. Also, leave the “Create a Rule for each of the following actions” setting selected. Click “Next”. You will see a confirmation page. Click “Finish” to create the rule set.
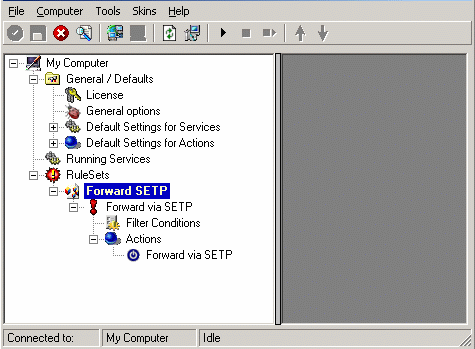
6. As you can see, the new Rule Set “Forward SETP” is present. Please expand it in the tree view until the action level of the “Forward SETP” Rule and select the “Forward by SETP” action to configure.
7. Now, type the IP address or host name of our central hub server in the “Servername” field:
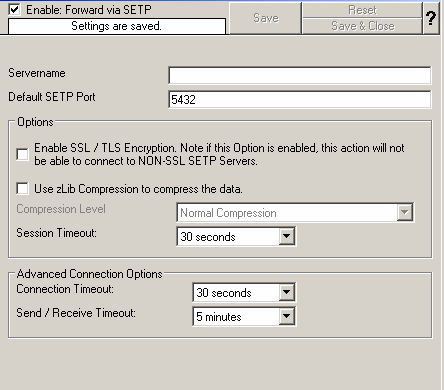
8. Make sure you press the “Save” button – otherwise your changes will not be applied.
This step needs only to be done on the central hub server!
1.Start the Application.
2. Again, you can select the language to use. And again, I suggest using English, as this makes the guide easier to follow.
3. Then define a new rule set, right click “Rules”. A pop up menu will appear. Select “Add Rule Set” from this menu. On screen, it looks as follows:
4. Then, a wizard starts. Change the name of the rule to whatever name you like. We will use “Database Logging” in this example. The screen looks as follow:

Click “Next”. A new wizard page appears as appeared in the case of EventReporter. Select only Database Logging here. Do not select any other options for this example. Also, leave the “Create a Rule for each of the following actions” setting selected. Click “Next”. You will see a confirmation page as showned in the case of EventReporter and there you have to click Finish.
5. After above steps you will see that the new Rule Set “Database Logging” is present. Please expand it in the tree view until the action level of the “Database Logging” Rule and select the “Database Logging” action to configure.
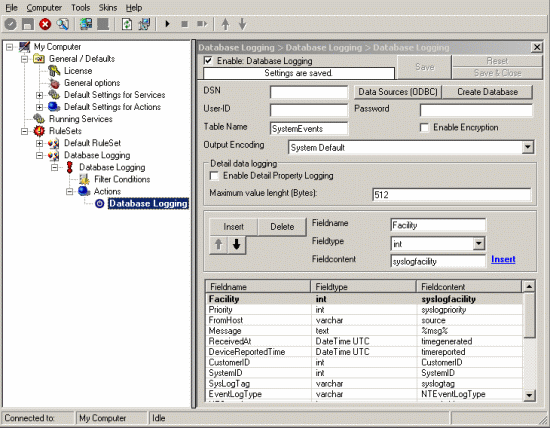
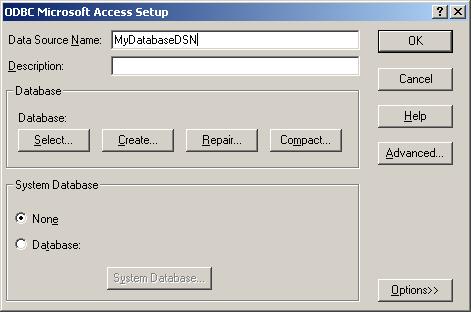
6. Now click on the Data Sources (ODBC) button to open the ODBC Data Source Administrator. Then choose the “System DSN” tab and click the “Add” button to add a new System-DSN (Select the Microsoft Access driver like in the screenshot below).
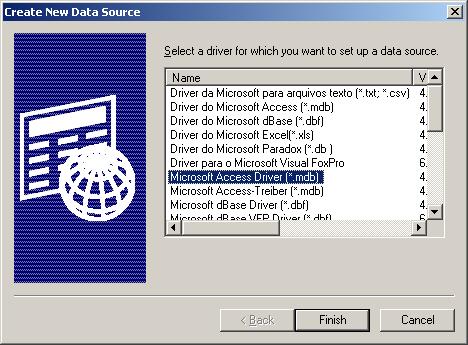
8. In the next step, click the “Select button” and go to the application installation directory (Usually C:\program files\instalationfolder\) and choose the sample database called sample97.mdb. After that name the new DSN with “MyDatabaseDSN” like in the following screenshot and press OK.
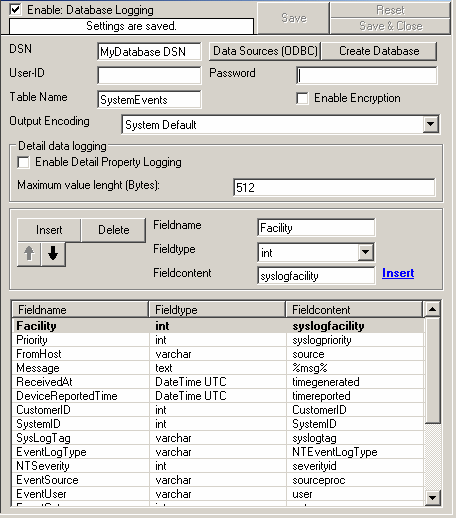
9. Now close the ODBC Data Source Administrator and switch back to the application client and insert “MyDatabaseDSN” in the DSN field. Leave all other settings in their default and save the changes.
The steps to configure the MonitorWare Agents are as follows (repeat this step on each of the 5 client machines and the central hub server!):
1. First, right click on “Services”, then select “Add Service” and then “Event Log Monitor”.

Once you have done so, a new wizard starts.
2. Again, you can use either the default name or any one you like. We will use “My Event Log Monitor” in this sample. Leave the “Use default settings” selected and press “Next”.

3. As we have used the default, the wizard will immediately proceed with step 3, the confirmation page. Press “Finish” to create the service. The wizard completes and returns to the configuration client.
4. Now, you will see the newly created service beneath the “Services” part of the tree view. To check its parameters, select it:

As you can see, the service has been created with the default parameters.
If you want to generate reports (using MonitorWare Console) on the data via this service i.e. EventLogMonitor, then you have to uncheck the “Use Legacy Format” option. This is recommended. If you don’t uncheck this option then meaningful reports aren’t generated (i.e. reports are not properly consolidated by MonitorWare Console).
Now, if you click Advanced Options button, you will see a pop up window as shown below:

If you want to generate reports (using MonitorWare Console) on the data via this service i.e. EventLogMonitor, then you have to uncheck the “Use Legacy Format” option. This is recommended. If you don’t uncheck this option then meaningful reports aren’t generated (i.e. reports are not properly consolidated by MonitorWare Console).
Now you must differentiate between clients and central hub server. In clients use the “Forward SETP” RuleSet we have created in Step 3, select it as rule set to use. In central hub server select the “Database Logging” RuleSet we have created in Step 4. Leave all other settings in their default.
Finally, save the change.
The steps to configure the agents are as follows (only central hub server!):
1. First, right click on “Services”, then select “Add Service” and the “SETP Server”.
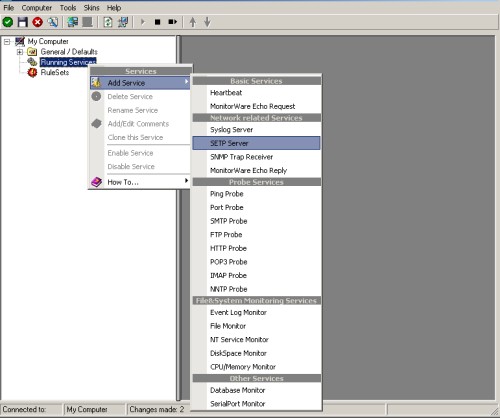
Once you have done so, a new wizard starts.
2. Again, you can use either the default name or any one you like. We will use “My SETP Server” in this sample. Leave the “Use default settings” selected and press “Next”.
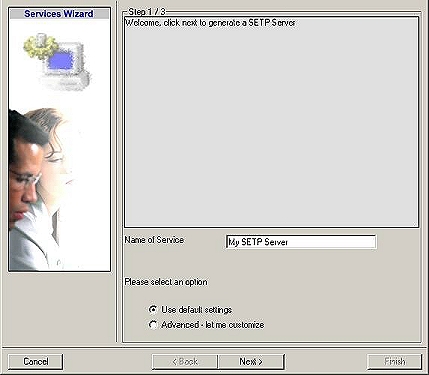
3.As we have used the default, the wizard will immediately proceed with step 3, the confirmation page. Press “Finish” to create the service. The wizard completes and returns to the configuration client.
4. Now, you will see the newly created service beneath the “Services” part of the tree view. To check its parameters, select it:
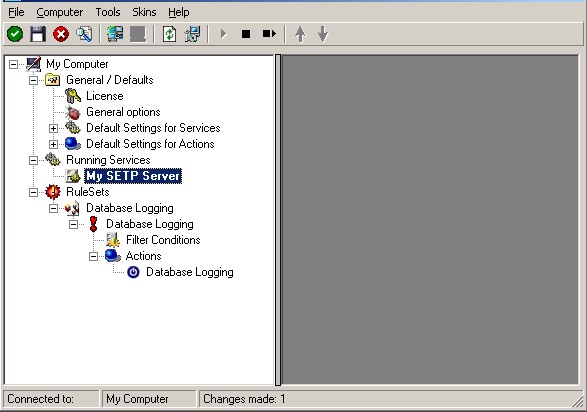
As you can see, the service has been created with the default parameters.
5. To use the “Database Logging” RuleSet we have created in Step 4, select it as rule set to use.
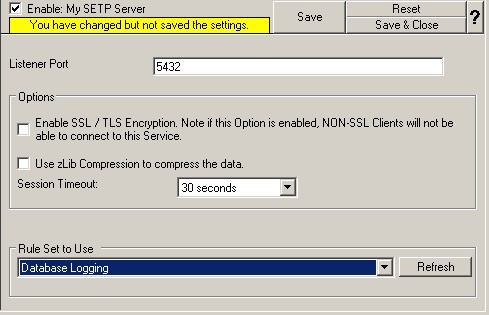
6. Last, save the change and then restart the application. This procedure completes the configuration of the SETP server.
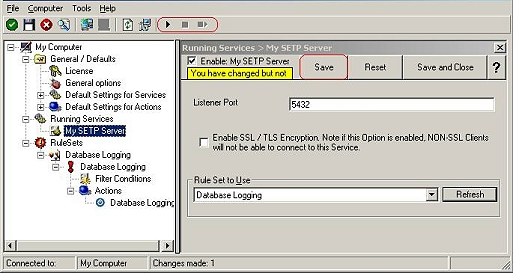
Application cannot dynamically read changed configurations. As such, it needs to be restarted after such changes.
MonitorWare Console publishes its reports through the local web server (central hub server). To avoid confusion, we recommend creating a separate directory on the web server for MonitorWare Console. Let us assume that you use Microsoft Internet Information Server and run it with the default configuration. Then, your web pages are stored in the c:\inetpub\wwwroot directory. Create a subdirectory “MonitorWareConsole” directly under this directory.
This section explains how the reports can be generated with MonitorWare Console manually. Since “System Status” Report is most comprehensive report that tells a detailed description about the network, in this section I will explain this report only. Please note that, the procedure for generating any report is almost the same.
This section explains how the reports can be generated with MonitorWare Console automatically using Job Manager. With Job Manager, you can generate all the reports based on a pre-defined schedule and ask it to either store it in some location on the hard disk or send it to specified recipient via email. Once again, I will explain the scheduling of System Status Report in this section. Please note that, the procedure for scheduling any report is the same.
Well, this is all you need to do to configure the basic operations. Once you are comfortable with the basic setup, you can enhance the system with local pre-filtering of event, enhanced logging and alerting (with MonitorWare Agent) and changing report options (with MonitorWare Console).
I hope this article is helpful. If you have any questions or remarks, please do not hesitate to contact us at support@adiscon.com.
Created 2005-06-23 by Hamid Ali Raja
The CPU monitor of MonitorWare Agent uses the Windows WMI System to query the CPU and memory related information from system. On Windows 2000, there is a known Windows Management Instrumentation (WMI) bug that reports continuously 98% of CPU usage. In this case you will need to install a Microsoft Hotfix to solve the issue.
You can get more details about this WMI bug and hotfix from the following link:
Created 2005-06-14 by Hamid Ali Raja
Last Updated 2006-04-27 by Timm Herget
How can I export my settings to a registry file?
To export your settings to a registry file, please do the steps described below.
Please note that you do NOT use the binary registryfile export-option!
Go to Computer menu and click Export Settings to Registry-file.

After step 1, you are shown a window as shown below to name and save your Registry file at your desired location. Please choose your file name and location where you want to save it.

If you have some zipping software installed, right click on the saved file and zip it, as shown below:

Send us the zipped file.

Note: You may be reluctant to send the registry file because of security reasons. We recommend you to review the contents of the registry file with notepad or any other text editor for security purposes.
Article created 2005-05-17 by Hamid Ali Raja.
In this scenario, a simple Syslog server will be created. No other services are configured. The Syslog server will operate as a standard Syslog server on the default port of 514/UDP. All incoming data will be written to a single text file.
The rule set specifies what action to carry out. You might be tempted to define the service first, but starting with the rule set makes things easier as it will be already present when the service is defined later and needs to be bound to a rule set.
To define a new rule set, right click “Rules”. A pop up menu will appear. Select “Add Rule Set” from this menu. On screen, it looks as follows:

Then,a wizard starts. Change the name of the rule set to whatever name you like. We will use “Write Syslog Log File” in this example. The screen looks as follows:

Click”Next”. A new wizard page appears:

There,select file logging. Do not select any other options for this example. Also, leave the “Create a Rule for each of the following actions” setting selected. Click “Next”.
This is just a confirmation page. Click “Finish” to create the rule set.
The wizard closes and the client shows a newly created rule set.

As you can see, the “Write Syslog Log File” rule set is now present. Please expand it in the tree view until you have the following screen contents:

As you can see, we have a “File Logging” action configured. We will review the settings just for your information. Click on “Filter Conditions”:

As you can see, none of the filter conditions are enabled. This means that the all information units (incoming messages) will be matched by these filter conditions. As such, the rules for the “File Logging” action will always be carried out.
Please note that this also means that all Syslog priorities and facilities will be written to the same file.
Now let us check the “File Logging” action itself. Please select it in the tree view:

As you can see, it has been created with the default parameters. Each day, a file will be created in the C:\temp directory and its base name will be MonitorWare. It will include all information items in the file.
If you would like to store it into a separate directory or change the file name, here is the place to do it. Important: please make sure the directory you specify exists! If it does not yet exist, please create it before you start the service. If the directory does not exist, the service is not able to store any files.
In our example, we would like to save it to “c:\logfiles” with a base name of “Syslog”. Therefore, we change these properties:

After doing so, you will notice the yellow text on top of the window. It tells you that the configuration changes have not yet been applied. To do so, press “save”.
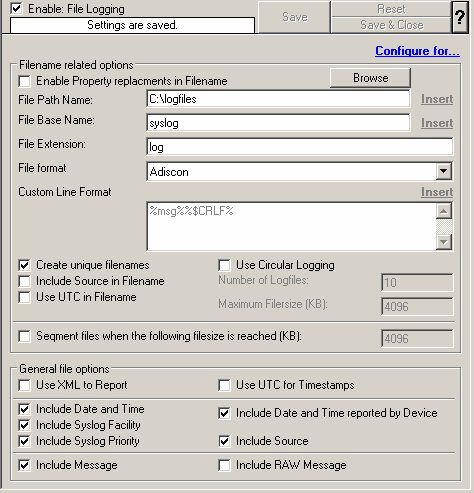
Now you have a workable rule set for logging incoming messages to a text file.
Now we need to define a Syslog server service. A Syslog server is also sometimes called a “Syslog daemon”, “Syslogd” or “Syslog listener”. It is the process that receives incoming messages.
To define it, right click on “Services”, then select “Add Service” and the “Syslog Server”:

Once you have done so, a new wizard starts:

Again, you can use either the default name or any one you like. We will use “My Syslog Server” in this example. Leave the “Use default settings” selected and press “Next”:
As we have used the default, the wizard will immediately proceed with step 3, the confirmation page. Press “Finish” to create the service. The wizard completes and returns to the configuration client. There, you will see the newly created service beneath the “Services” part of the tree view:
To check its parameters, select it:
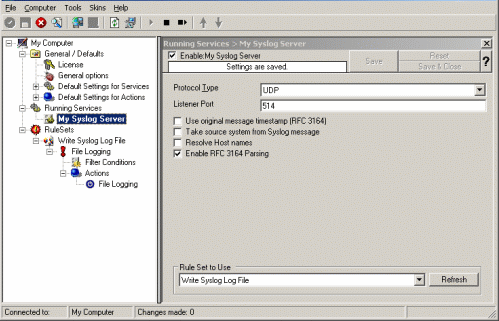
As you can see, the service has been created with the default parameters. As such, it operates as a RFC compliant standard Syslog server.
Please note that the “Write Syslog Log File” has been automatically assigned as the rule set to use. This is the case because we already created it and it is the only rule set. By default, the wizard will always assign the first rule set visible in the tree view to new services. If another one is to be used, you need to change it to the correct one here in the service definition.
Also, note that the wizard uses the default properties from the “Service Defaults”. Obviously, if these are changed, the default properties for new services will differ.
This procedure completes the configuration of the Syslog server.
Application cannot dynamically read changed configurations. As such, it needs to be restarted after such changes. In our example, the service was not yet started, so we simply need to start it. If it’s already running, you need to restart it.
Service control can be done with both the respective operating system capabilities (like service manager MMC) or with the configuration client. These are shown in the red surrounded area in the following screen shot:

The buttons resemble Windows service manager – start, stop and restart. In this example, stop and restart are grayed out because the service is not running.
After service restart, the new definitions are active and application is ready to accept and store incoming messages.
Even though application is now ready, it can only receive messages if some devices send them. Remember, Syslog is a protocol where the server is passively waiting for incoming messages. As long as no device sends message, the Syslog server will not log anything.
Since there are a large variety of devices, we unfortunately cannot provide device specific instructions. However, almost all devices need to be configured with their specific configuration tool. Typically, only two settings need to be made: one to activate Syslog messages at all and one with the Syslog server IP address or name.
For some devices, we have step-by-step guides. Please read “Sample Syslog Device Configurations” for further details.
Remember: the computer running application now acts as a Syslog server. As such, you need to find out its IP address or name and supply it to the device as the Syslog server. Please note that not all devices can operate with computer names. Use the IP address, if in doubt.
Article created 2005-05-05 by Hamid Ali raja.
1.
Start the Application.
2.
Select your language – in this example, I use English, so it might be a good idea to
choose English even if that is not your preference. You can change it any time
later, but using English makes it much easier to follow this guide here.
3.
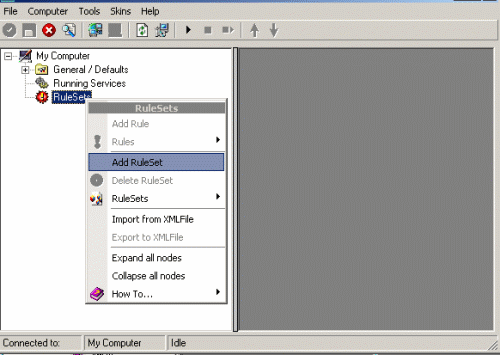
Then define a new rule set, right click
"Rules". A pop up menu will appear. Select "Add Rule Set" from this
menu. On screen, it looks as follows:
4.
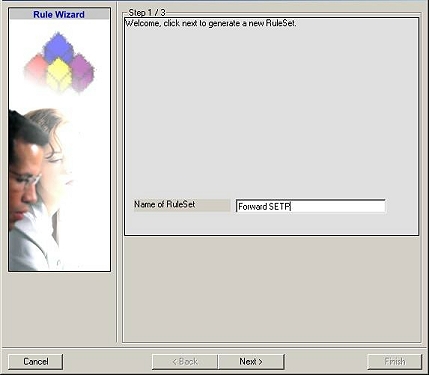
Then, a wizard starts. Change the name of the
rule to whatever name you like. We will use "Forward SETP" in this example.
The screen looks as follow:
Click "Next". A new wizard page appears.
5.
Select only Forward by SETP. Do not select any
other options for this sample. Also, leave the "Create a Rule for each of the
following actions" setting selected. Click "Next". You will see a
confirmation page. Click "Finish" to create the rule set.
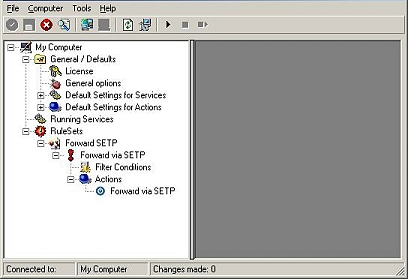
6.
As you can see, the new Rule Set "Forward
SETP" is present. Please expand it in the tree view until the action level of
the "Forward SETP" Rule and select the "Forward by SETP" action to
configure.
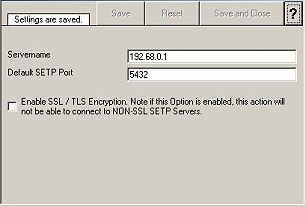
7.
Now, type the IP address or host name of our
central hub server in the "Servername" field:
8.
Make sure you
press the “Save” button – otherwise your changes will not be applied.