Monitoring MS ISA Firewall Logfiles via syslog
Created 2007-04-02 by Florian Riedl
Information for the usage of this guide. This guide will give you the hints to create a configuration to monitor ISA server logs as well as forward all log data to a syslog server. To make things easier, the guide is split up into several mini-guides, which will each cover one big step of the configuration. These mini-guides only describe the general procedure. You may have to adjust settings like IPs to your personal needs.
Please note: In order to forward the ISA Firewall logs you need MonitorWare Agent.
Further you need to setup your ISA server to log into textfiles. Please review the manual for further instructions. Important: Please ensure that the log format will be W3C logfile format. This is for compatibility reasons.

The scenario looks like this. The configuration we are going to make represents the first machine on the left side.
Step 1
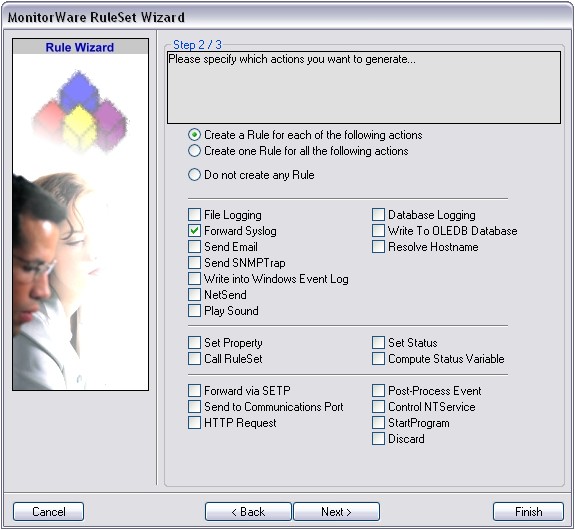
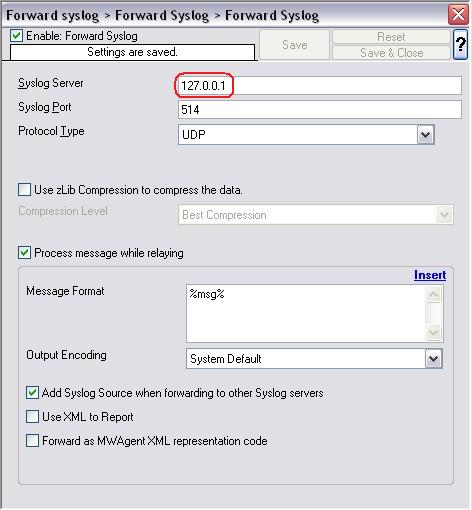
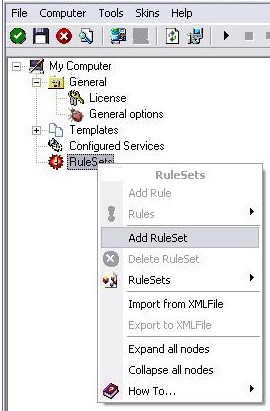
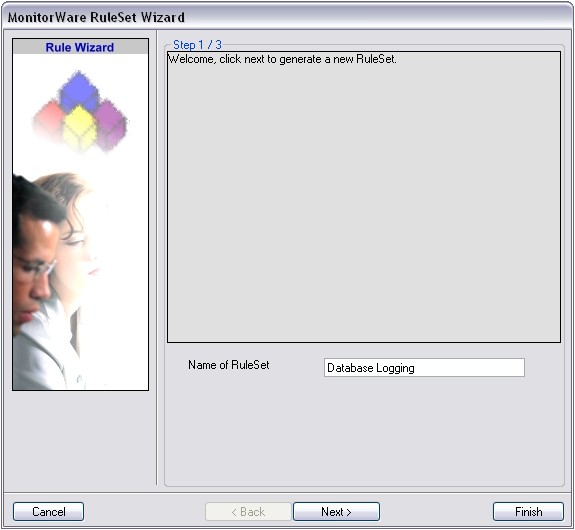
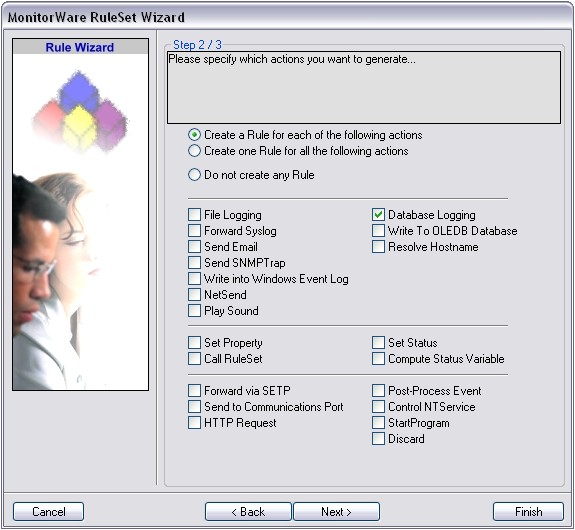
The first step we are gonna take is to create a RuleSet with the corresponfing action. In this case we want to forward our logs via syslog. Therefore we need a “Forward via syslog”-Action. Instructions on how to create a ruleset and setup the action can be found here:
How to Setup a Forward via Syslog Action
Please Note:This is a general guide, you may have to adapt some steps.
Step 2
The next important step is to setup the FileMonitor. We need it to monitor the textfile logs created by your ISA server.
How to Setup the FileMonitor Service
Please Note:This is a general guide, you may have to alter the path- and filename.
Step 3
The last and final step is to click on the Save button if necessary and then start MonitorWare Agent. You are now done. Finally you should receive all the log entries of your EventLog as well as from your ISA Firewall on your syslog server.